Apps & tokens
Overview
Seequent Evo integrations need a user's consent to access data using Seequent APIs and SDKs. Evo uses OAuth 2.0 to grant access, and an app registered with the iTwin Platform provides the means to initiate the OAuth process.
Before you can create an access token you must first register your app. During registration you must provide basic information such as the app name and redirect URI, which redirects users to the appropriate web server, browser, or native app.
Requirements
To register an app you must have:
- A Bentley user account that belongs to an organisation with Evo entitlements.
- Access to the Bentley iTwin Developer Portal.
- Sufficient permissions to register or modify applications, e.g. the developer role at a minimum.
- A method to securely store the app credentials that are generated.
About Evo access tokens
Access tokens are digital keys used to verify and authenticate a user's identity before granting access to resources. Access tokens are essential for secure authentication and authorisation processes, ensuring that only authorised users can access specific data or functionalities.
Scope is a mechanism in OAuth 2.0 to limit an application's access to a user's account. An application can request one or more scopes and the access token issued to the application will be limited to the scopes granted. Apps registered in the iTwin Developer Portal will include a set of Evo and iTwin scopes.
When requesting an access token you must include a list of scopes. Consult the list below to determine which scopes you need to include.
Required Evo scopes
You should always include these scopes in your OAuth requests because they provide access to critical Evo APIs.
evo.discoveryto access the Evo Discovery API.evo.workspaceto access the Workspaces API.
Optional Evo scopes
Include these scopes to your OAuth requests if you intend to work with the corresponding Evo API.
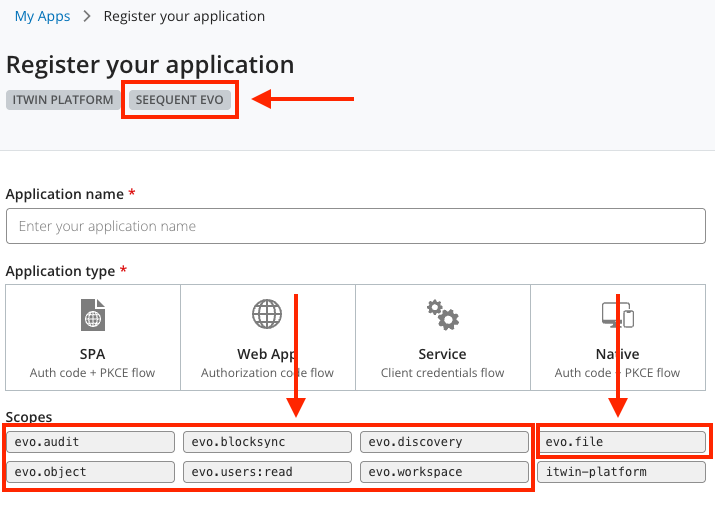
evo.blocksyncto access the Block Model API.evo.fileto access the File API.evo.objectto access the Geoscience Object API.
Optional additional scopes
OAuth apps can refresh a user's access token without requiring the user to sign-in again. This functionality is only available when you include the offline_access scope in your OAuth request. This feature is not available (or required) when using a machine-driven or service app.
Secure storage of app credentials and tokens
Before registering a new app, we highly recommend that you have a secure way to store your app credentials. Securely storing your credentials is important because the app is the door by which your valuable data is accessed. App credentials, and the access tokens that the app creates, should be treated just like any other password.
Hints for securely storing app credentials
- Don't share app credentials with colleagues over email or internal messaging systems. Instead, credentials should be stored in a secure password manager.
- The credentials of a service identity (from a service or machine-driven app) are particularly sensitive, since a bad actor who obtained those credentials could easily access any Evo data available to the service identity.
Hints for securely storing access tokens
- Access tokens should never be committed to source control, e.g. to a GitHub repository. Take advantage of pre-commit hooks and other security tools to prevent the accident leakage of access tokens.
- Always save access tokens to a
.envfile in your project folder or to your system environment directly instead of hard-coding tokens into your source files. - Never expose access tokens in error messages or log files.
App types
Choose an app that best suits your development requirements.
-
User-driven apps require a real person to sign-in. Since the access token represents this person, any interactions with Evo will be attributed to them.
The iTwin Platform supports these app types for user-driven authentication:
-
Machine-driven authentication does not require a real person to sign-in. Instead, a service identity is created which has its own unique profile and email address. The service identity must be added to your Evo instances and to your Evo workspaces just like a regular user.
The iTwin Platform supports the following app type for machine-driven authentication:
- Service — a machine-to-machine application requiring no user interaction.
User-driven app
Register the app
User-driven apps require the user to periodically re-authenticate to renew the access token, so this type of app may not be suitable for machine-driven scripts. If you need your scripts to run without any user interaction, register a machine-driven app instead.
-
Visit https://developer.bentley.com/ and sign in.
-
Click your profile in the top-right corner and select My Apps. You may need to agree to Bentley developer terms before proceeding.
-
Click the dropdown arrow on the Register New button and choose Register new app for Seequent Evo.

-
Confirm that the application is a Seequent Evo app. You can do this by verifying that "Seequent Evo" is under "Register your application", and by checking the listed scopes include Evo services.
-
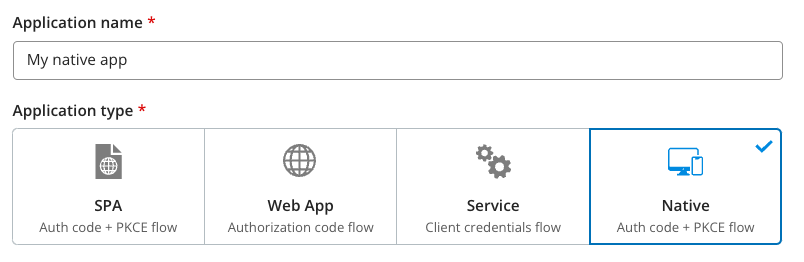
Enter an application name and select one of the options: Native/SPA/Web App.
-
Add additional application owners, if required.
-
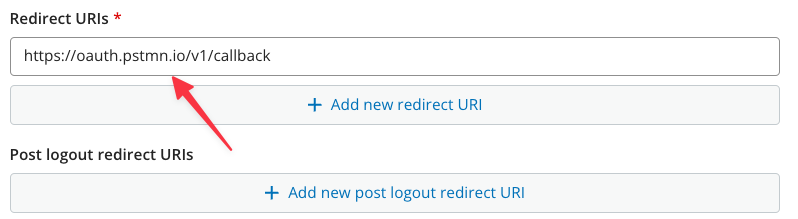
Enter one or more redirect URIs (required) and logout redirect URIs (optional). In this example we are adding the redirect URI for the API testing tool Postman. The redirect URI will differ depending upon your development environment, e.g. enter http://localhost:3000/signin-callback for running your app locally.
-
Click Register.
-
The next screen displays the unique Client ID of your application. Be sure to save the client ID in a secure place. You will receive a confirmation email stating that your new application was successfully registered.
Machine-driven app
Register the app
Data published to Evo using a service application will be associated with a service identity. If you need data to be directly associated with the user who made the API calls, register a user-driven app that requires a user to sign-in with their own credentials.
-
Visit https://developer.bentley.com and sign in.
-
Click your profile in the top-right corner and select My Apps. You may need to agree to Bentley developer terms before proceeding.

-
Click the dropdown arrow on the Register New button and choose Register new app for Seequent Evo.

-
Enter an application name and select the option Service: Client credentials flow.

-
Add additional application owners, if required.

-
Click Register.
-
A pop-up window displays the newly created client ID and client secret for your application.
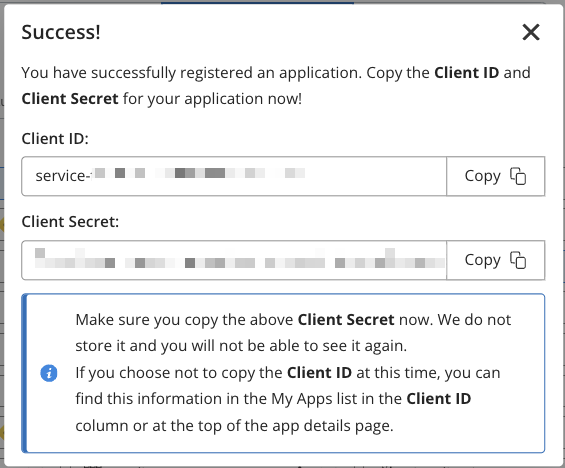
Close the window after you have saved a copy of the client secret.
-
The next screen displays the client ID and an auto-generated client email that is unique for your application. On this screen you can edit details of your application and regenerate the client secret if required. You will receive a confirmation email stating that your new application was successfully registered.

-
Click the buttons next to the client ID and client email to copy them. Be sure to save these credentials in a secure place.
Add the service identity to your Evo instance
Just like adding a new colleague to your Evo instances, your new service identity must be added to the Evo instances where you intend to utilise Evo services.
Contact your Evo instance administrator, send them the client email of your new service identity, and inform them that this new account will be used to integrate with Evo services.
Only after the service identity has been added to an Evo instance should you proceed to the next step.
Add the service identity to an Evo workspace
The service identity must also be assigned to any Evo workspace that the identity needs to access with the Seequent Evo APIs.
-
Sign in to the Evo portal.
-
In the Workspaces tab click to open the appropriate workspace.
-
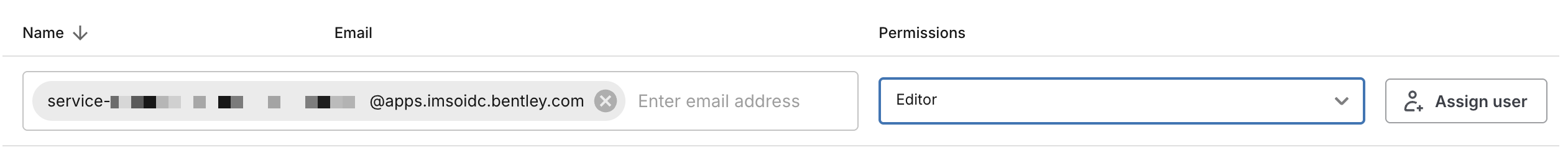
Click the Permissions tab.

-
Click the Enter email address box and paste the email of the service identity. Give the service identity the appropriate user role and click Assign user. If the identity will be publishing new data, assign the Editor role, otherwise, assign the Viewer role.
How to delete users and change application owners
-
Sign in to the User Management Portal, select the checkbox next to the relevant user(s), and click the bin icon to delete.
-
Visit My Apps, select the application for which you want to change the owner, click the X button to remove the current owner, and then add the new owner.
Creating and managing access tokens with Python
Seequent actively maintains open-source projects on GitHub that make it easy to build an Evo integration using Python.
Visit Evo Python SDK to learn how to install and use the SDK.
If you are building you integration in a language other than Python, you can still learn Evo programming concepts by visiting the link above.